Ever felt overwhelmed by the vast amount of information you need to study for the AWS certification exam, specifically when it comes to VPC? I’ve been there, and like many others, struggled to grasp the intricacies of this vital service. Fortunately, while preparing for my exam, I found some key notes that significantly improved my understanding.
In this post, I’m excited to share these notes with you, offering a clear and concise overview of VPC. We’ll dive into its core components, explore connectivity options, and wrap up with essential “good to know” tips. Whether you’re a complete beginner or someone seeking a refresher, this post aims to demystify VPC and prepare you for your AWS certification journey.
Well, let’s begin with the definition of VPC. A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS Cloud. You can launch AWS resources, such as Amazon EC2 instances, databases, into your VPC.
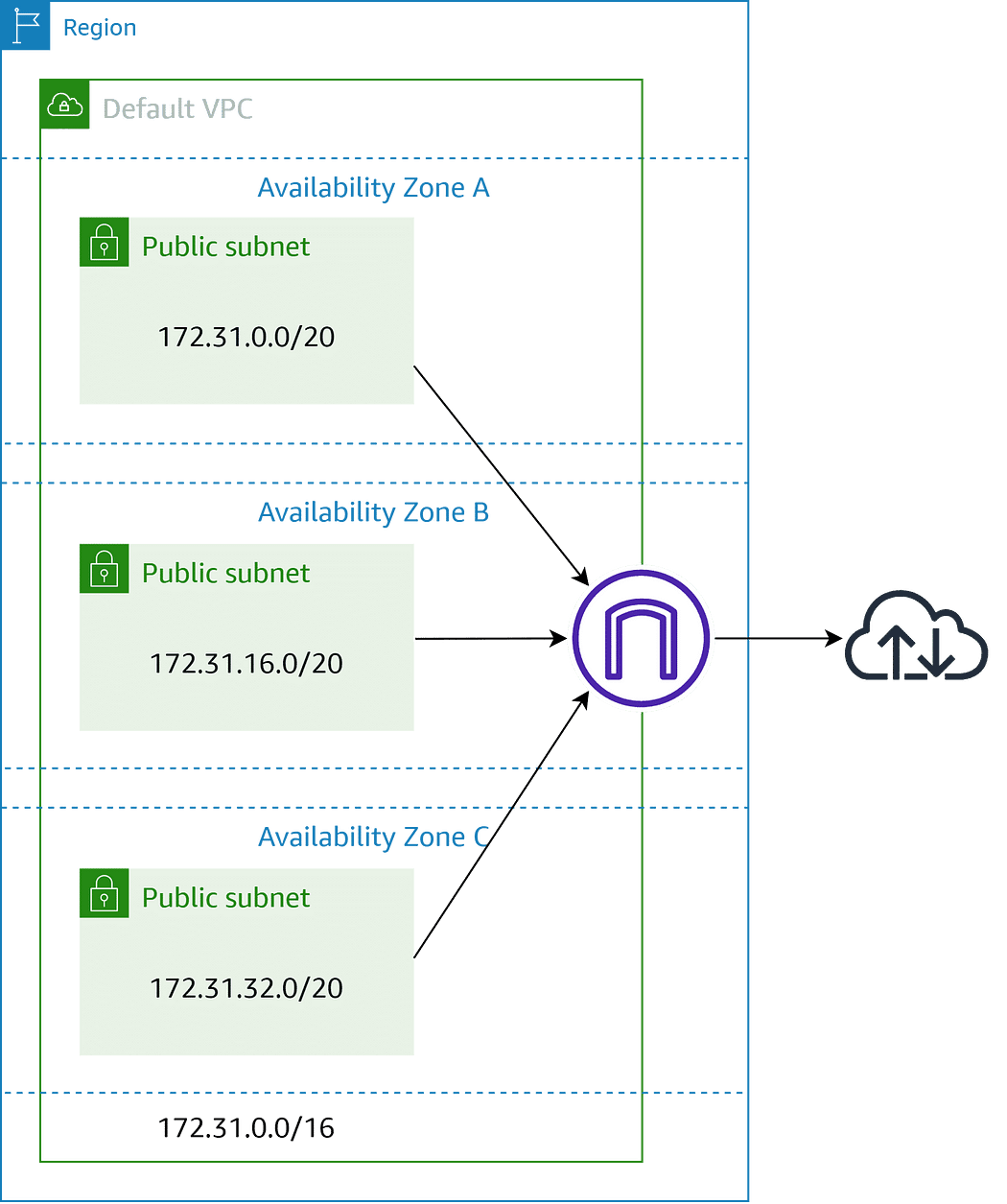
VPC is a regional service. To start, AWS provides a default VPC that comes with public subnet in each availability zone, default Network ACL, default Security Group, Main route table, an internet gateway already configured and settings to enable DNS resolution.
The non-default VPC that you creates is an isolated network that do not allow anything in or out without explicit configuration.
As shown in the AWS VPC console, Subnets are how you add structure and functionality to your Amazon VPCs, and they are an Availability Zone resilient feature of AWS.
A subnet is a sub-network of your Amazon VPC CIDR range that is created in one Availability Zone. The are a range of IP addresses in your VPC. You can launch AWS resources, such as EC2 instances, into your subnets. Each subnet resides entirely within one Availability Zone.
When assigning CIDR to the Subnet, the first 4 IP addresses and the last IP address are reserved to the VPC and used for Network Address, VPC router, mapping to amazon-provided DNS, for future use, the last is for broadcast.
You can create the following resources for your VPC: custom Network ACL, route table, SG, Internet Gateway, NAT GW
Components in a VPC
- CIDR: CIDR is based on the idea of subnet masks. A mask is placed over an IP address and creates a sub network. The subnet mask signals to the router which part of the IP address is assigned to the hosts and which determines the network
- Subnet that runs in One Availability Zone AZ. In case of AZ failure, the subnets and all running services inside it will fail. For high availability, it’s recommended to pace services in different subnets from different AZs.
- EC2 are virtual servers that provide scalable computing capacity while eliminating the need to invest on hardware. EC2 instance is launched in a private or public subnet within the VPC. The instance receives a primary private IP address from the IPv4 address configured for the subnet.
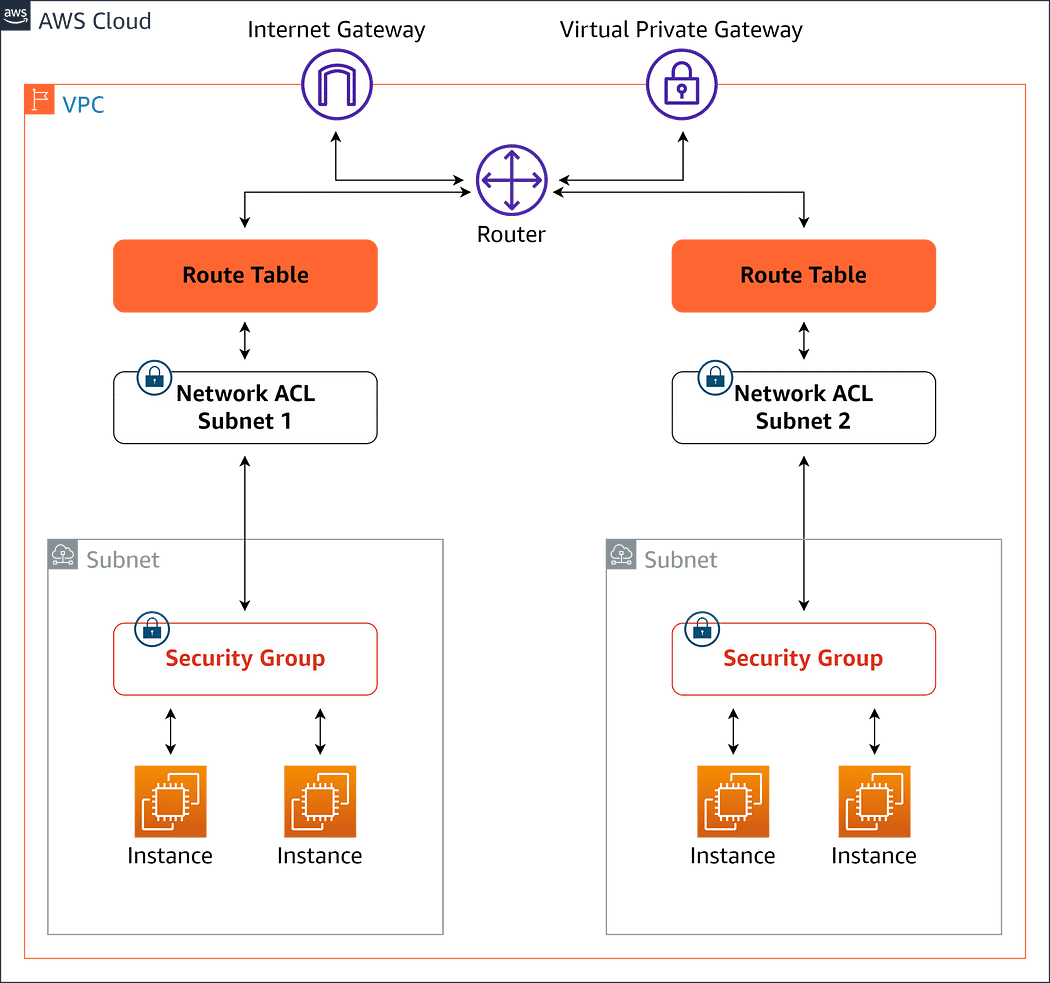
- A VPC Router is highly available and moves traffic from A to B. The router runs in all your Availability zones that your Amazon VPC uses. The router has a network interface in each subnet and uses the first reserved IP address of the subnet. the router is fully managed by AWS to route traffic between subnets in your VPC.
- Route table that contains a set of rules called routes that determines where network traffic from subnet or gateway is directed. They are created at the VPC level, but are associated with a subnet. If you don’t associate a new route table to your subnet, then the main route table is associated. Only one route table can be associated with a subnet, but it’s possible to use the same route table for many subnets at a time.
- Internet Gateway sits on the edge of your VPC and allow traffic to and from the Internet. A VPC can have only One Internet Gateway IG, and it’s regional. It works across all Availability zones. Once created, the IG should be attached to the VPC and added to the route table for the subnet that becomes public.
- Network Access Control List NACL is a type of security filter that filter traffic that enters and leave a subnet. A NACL is attached to a subnet. Hence, it only manages traffic that is crossing the subnet boundary but not internal traffic. Network ACLs are stateless, which means that if you add a rule to allow/deny an inbound traffic, then you must also add the same rule for outbound traffic.
- Security Groups are another security feature that complement the NACL. It handles security outside the subnet but also the interaction inside the subnet. Security groups are attached to the elastic network interface of AWS resources in the subnet. It sits at the boundary of EC2 instances. Security groups are stateful and view traffic as one stream. If traffic is allowed in, then that traffic is automatically allowed back out.
Connectivity
The different connectivity option for the VPC are:
- The internet via an internet Gateway (One per VPC)
- Your corporate data center using Site-to-site VPN connection (using Virtual Private Gateway)
- Other AWs services (via internet gateway, VPC endpoints, virtual private gateway)
- Other VPCs in the same or different region as well as same or different account via VPC peering or transit gateway
Good to know:
- CIDR (Classless Inter-Domain Routing) allocated to VPC are the private one (Class A: 10.0.0.0, Class B: 172.16.x.x, Class C: 192.168.x.x).
- Subnets can’t span across multiple AZs
- Max CIDR per VPC is 5.
- CIDR should not overlap within your other networks
- For resiliency, it is recommended to provision subnets in at least 2 AZs.
- You cannot increase or decrease the size of an existing CIDR block that’s associated with the VPC.
- You assign a single CIDR IP Address range as the primary CIDR block for the VPC and can add up to 4 secondary CIDR. Subnets within a VPC are addressed from these CIDR ranges by you.
- It’s also possible to shrink the network by removing secondary CIDRs.
- While you can create multiple VPCs with overlapping IP address ranges, doing so will prohibit you from connecting these VPCs (example via VPC peering). For this reason it’s recommended using non-overlapping IP address ranges.
- CIDR IP address range for VPC can be between /28 (in CIDR notation) and /16 in size.
- The minimum size of a subnet is a /28 (or 14 IP addresses.) for IPv4. Subnets cannot be larger than the VPC in which they are created.
- Amazon reserves the first four (4) IP addresses and the last one (1) IP address of every subnet for IP networking purposes.









No comments :
Post a Comment