Imagine sending your data on a private jet ✈️ instead of a bus 🚌 through rush hour traffic 🚦. That’s the magic of VPC endpoint: a secure, high-speed lane connecting your AWS resource directly to specific services, all within the safe confines of the AS network.
This blog post is your-first class ticket to understanding these powerful tools and get ready for you AWS certification. Buckle up and we will explore the two types of VPC endpoints:
- Interface endpoints: Think of them as private tunnels, shipping data directly to the service without ever touching the public internet.
- Gateway endpoints: these acts as secure gateways, allowing communication with AWS S3 and DynamoDB.
As explained before, a VPC endpoints lets you privately connect your VPC to supported AWS services and VPC endpoint services.
VPC endpoints are virtual devices. They are horizontally scaled, redundant, and highly available Amazon VPC components that allow communication between instances in an Amazon VPC and services without imposing availability risks or bandwidth constraints on network traffic.
Gateway endpoints
A gateway endpoint is a virtual connection within your VPC that allow resources in your VPC to directly access AWS S3 and DynamoDB. The gateway targets specific IP routes in an Amazon VPC route table, in the form of a prefix-list, used for traffic destined to Amazon DynamoDB or Amazon Simple Storage Service (Amazon S3).
When you create a gateway endpoint, you select the VPC route tables for the subnets you enable. A route with a prefix-list is automatically added to each selected route table. Those routes can’t be modified or deleted unless you disassociate the route table from the gateway or you delete the gateway itself.
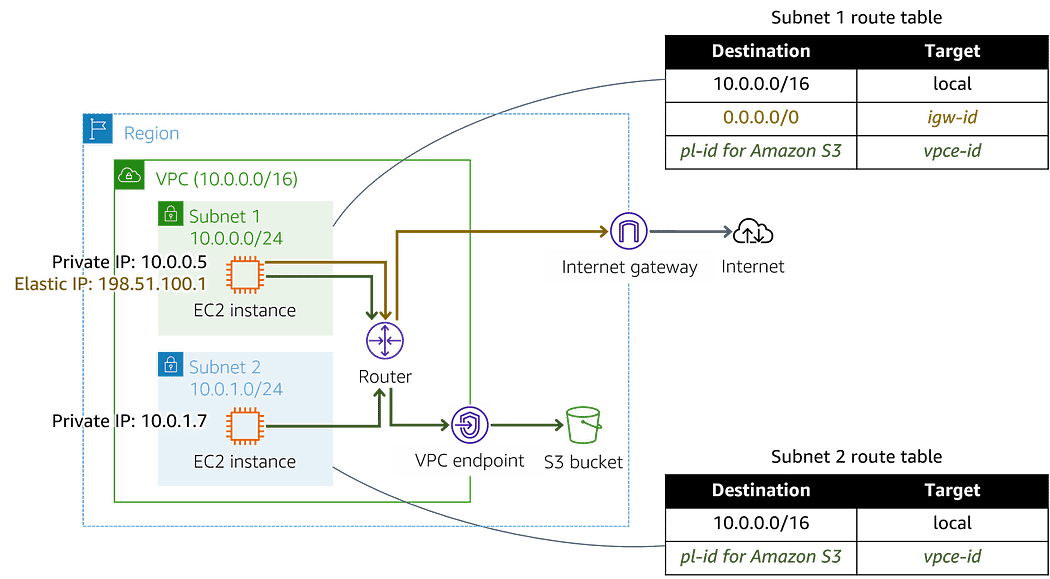
There is no additional charges for using the gateway endpoint, which makes it preferable over interface endpoint in case your need access to S3 or DynamoDB. Nevertheless, Gateway endpoint doesn’t allow access from on-premise networks, from peered VPC in other regions and through transit gateway. For those use cases, you must use the Interface endpoint.
Here short tips when working with the gateway endpoints:
- A gateway endpoint is available only in the region you created it. Be sure it’s the same region as your S3 bucket.
- You can have routes to S3 and/or DynamoDB in the same route table. But you can’t have multiple routes to the same service in a single route table.
- The instances access S3 or DynamoDB service using its public endpoints. Their security groups must allow traffic to and from the services using the prefix_list_id as destination with the TCP protocol on port 443.
- The Network ACLs for the subnets for theses instances must also allow traffic to and from the services.
You need to consider the AWS specificities in traffic routing. AWs uses the most specific route that matches the traffic to determine how to route it (longest prefix match). In route tables with endpoint route this means:
- If the route that sends all internet traffic (0.0.0.0/0) to an internet gateway, the endpoint route takes precedence for traffic sent to S3 or DynamoDB in the current region.
- Traffic destined for S3 or DynamoDB in a different region goes to the internet gateway as prefix lists are specific to a Region.
- If there is a route that specifies the exact IP address range for the S3 or DynamoDB in the same region, that route takes precedence over the endpoint route.
Interface endpoints
Interface endpoints enable connectivity to services over AWS PrivateLink.
But wait, what is PrivateLink. It’s an amazing service that allows you to to securely connect your resources in an Amazon Virtual Private Cloud VPC to specific AWS resources, other VPCs, and even on-premise applications, without ever exposing your data in the public internet.
Here some benefit of the PrivateLink:
- AWS PrivateLink gives on-premises networks private access to AWS services through Direct Connect.
- You can make services available to other accounts and VPCs that are accessed securely as private endpoints.
- If you use AWS PrivateLink with a Network Load Balancer to route traffic to your service or application, clients can connect to any service you host.
- Services configured to support AWS PrivateLink can be offered as a subscription service through the AWS Marketplace.
The interface endpoint is powered by the AWS PrivateLink. When configuring an interface VPC endpoint, an elastic network interface (ENI) with a private IP address is deployed in your subnet. This ENI acts as an entry point for traffic destined to a supported service. Remember, attaching a Security Group is crucial for access control.
Provisioning an interface endpoint incurs hourly charges based on its uptime and data processing.
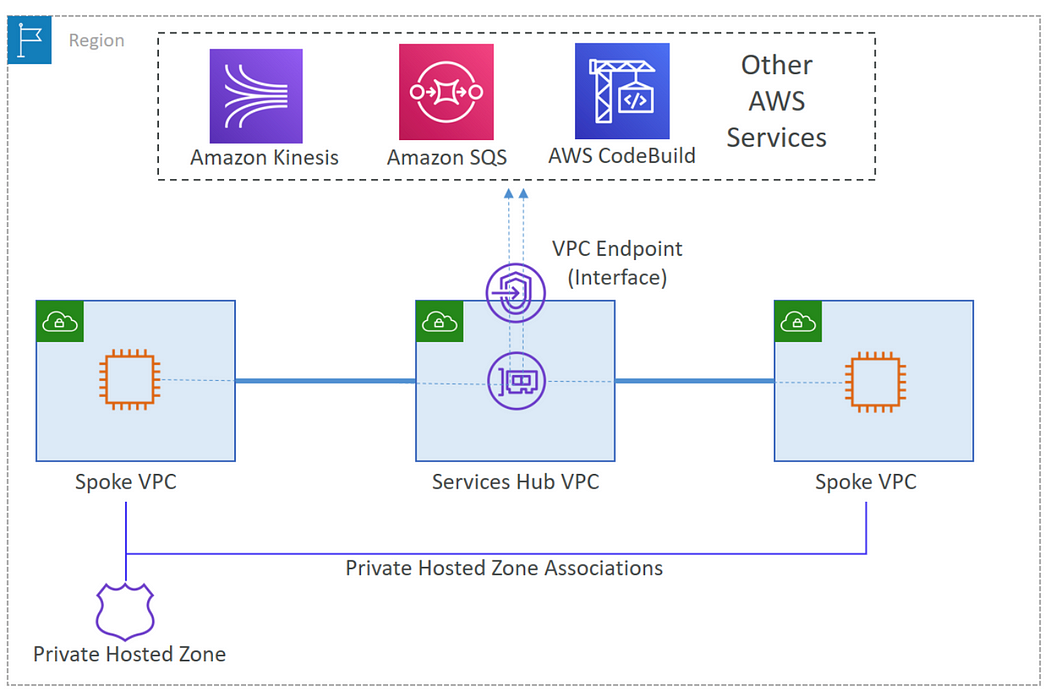
To optimize costs and simplify management, consider hosting interface endpoint in a centralized VPC. All the “spoke” VPCs can then leverage these centralized endpoints via Transit Gateway or VPC peering, eliminating the need for individual endpoints in each VPC. This approach known as Centralized VPC endpoint architecture pattern, minimizes costs and streamlines access control with centralized Security Groups.
P.S. Don’t forget to share your thoughts and experience with VPC endpoints in the comment below!








No comments :
Post a Comment